As lots of you’re involved with blockchain being hacked, we’ll dive into the core of the problems to know whether or not one of these situation is even attainable.
We live in a world the place safety is a big concern, and information breaches occur to be a every day exercise. The web infrastructure that we use these days is turning into out of date day-to-day. It could possibly’t clearly forestall any form of high-end cyber-attacks. It doesn’t matter what sort of cybersecurity we’re utilizing, it undoubtedly can’t shield us 100%.
Blockchain know-how occurs to vow a unique strategy on this method. It ensures that we now not must rely on belief and may management our digital content material ourselves. Furthermore, in a means, many declare that nobody can hack the blockchain. However is that assertion actually true?
Is there no means one can hack blockchain? In actuality, blockchain is very highly effective and may look like nobody can hack blockchain. Nonetheless, we’ve got to say, it’s not totally resistant to assaults. Each single know-how comes with sturdy and weak factors. Thus, we’ll be digging a bit deeper and allow you to know can blockchain be hacked or not.
However earlier than we start, let’s take a look at just a few of the most important blockchain hack on-line that occurred over time. So, let’s begin!
Blockchain Hacked: Can You Hack Blockchain?
First Blockchain hack on-line in June 2011.
Loss: $50,000 (2609 BTC)
This is likely one of the well-known blockchain hacked situation in historical past. Apparently, the cyber-criminal bought ahold of the auditor’s credentials after which misused these to get into the system. Extra so, the attacker then modified the worth of 1 BTC to 1 cent. Moreover, the attacker additionally collected 2609 BTC from a number of shoppers that bought the BTC at this very low worth.
After that, he/she even bought again 650 BTCs from one other account as nicely. After the hacking blockchain situation got here to gentle, Mt. Gox stopped all operations for a few days. Nonetheless, then they restarted the operations and carried on.
Now, let’s transfer on to the following assault of this could you hack the blockchain information.
Construct your identification as a licensed blockchain skilled with 101 Blockchains’ Blockchain Certifications designed to offer enhanced profession prospects.
Second Blockchain hacked in March 2014.
Loss: $350 million (750,000 BTC)
The second assault was even worse for Mt. Gox. Apparently, this time, the attacker came upon a few bug within the codes and noticed that transactions are extra versatile. Extra so, anybody might edit the element of the transaction and make it appear to be that it by no means even occurred. So, form of like double-spending.
If we go into extra element, the method occurred like this. The attacker manipulated the sender’s signature earlier than it was saved completely within the ledger. He/she additionally modified the transaction ID. The brand new ID and adjusted transaction can overwrite the unique transaction particulars and make it appear to be that the receiver didn’t get any funds.
Nonetheless, in actuality, the attacker did obtain it, however the system mistook it for an unsuccessful transaction. As soon as it’s accomplished, the attacker then requested for the switch once more and bought the funds two occasions.
This time Mt. Gox halted the entire BTC transactions instantly after the detection of the cyber-attack. Extra so, there have been no refunds as nicely. After a while, they couldn’t deal with the loss after which filed for chapter.
General Loss: $430,000 (122,000 BTC)
First Blockchain hack on-line in March 2012.
Within the first one, the attacker primarily attacked Bitcoinica’s scorching pockets and decrypted it from Linode’s server. In the long run, the assault took about 43,554 BTC. Different customers who had been additionally utilizing Linode’s server bought hacked too.
The Second Blockchain hacked in Could 2012.
Properly, the primary time wasn’t sufficient for Bitcoinica. The second time, the attacker bought into the inner system of the database. From there, he/she stole all of the customers’ personal info and even took 38,000 BTC.
Third Blockchain hack in July 2012.
The assaults bought so unhealthy that, that in a while in July, they stole round 40,000 BTC once more! Nonetheless, they occur to retailer their funds secretly in Mt. Gox secretly, they usually had been later refunded.
Let’s transfer on to the following one on this are you able to hack blockchain information.
Blockchain hack on-line in August 2016.
Loss: $72 million (120,000 BTC)
The story is sort of quick on this one. Bitfinex began to make use of BitGo’s multi-signature pockets only a 12 months in the past earlier than the assault. Apparently, the pockets had some main points, and there have been some large vulnerabilities in it. In actuality, the attacker discovered the problem and stole the BTCs.
After the assault, the corporate shortly issued BFX tokens for compensating their clients. BFX tokens are redeemable in USD. Nonetheless, they refunded all of the stolen cash step by step because it was a hefty sum. With simply this one assault, the value dropped from $607 to $515 inside just some hours!!!
Blockchain hack on-line on 6th December 2017.
Loss: $80 million (4700 BTC)
It’s extra of a current assault on blockchain. Apparently, the Slovenian trade platform, NiceHash, was hacked. Quickly after the blockchain hack, the CEO got here into Fb Dwell and introduced it. Nonetheless, he didn’t get into way more element.
All we all know thus far that one among their worker’s computer systems was compromised, and the attackers used that to steal the cash.
In actuality, the corporate suspended all of the transactions for the following 24 hours to investigate the problem and the way they will forestall it from ever occurring once more. Now we have to say, it’s a slightly good initiative from the corporate administration.
So, these are a few of the blockchain hacks that occurred up to now. Now, let’s transfer on to the following section of this could you hack blockchain information.
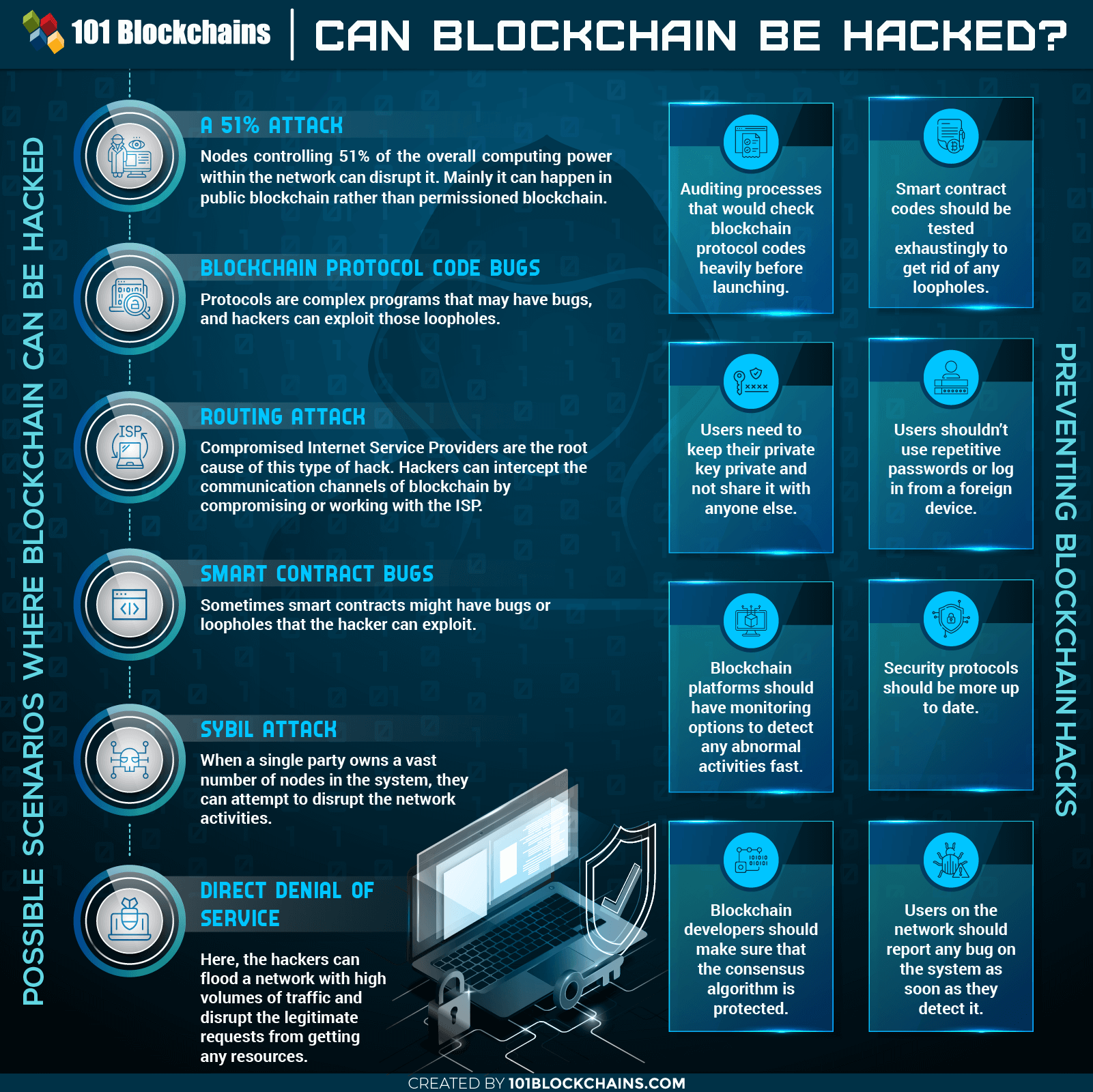
Hacking Blockchain: Attainable Situations
Please embrace attribution to 101blockchains.com with this graphic. <a href="https://101blockchains.com/blockchain-infographics/"> <img src="https://101blockchains.com/wp-content/uploads/2019/10/Can-blockchain-be-hacked.png" alt="Can blockchain be hacked="0' /> </a>
Now we’ll talk about if blockchain may be hacked and, if that’s the case, how it may be attainable. Some particular situations might happen. Let’s see what they’re –
Let’s begin off with the essential hacking blockchain situation. You probably have been coping with blockchain for enterprise a while, then you will need to have heard concerning the 51% assault scheme. However how can a 51% assault occur?
Let’s say there’s a public blockchain or DLT that makes use of Proof of Work consensus and occurs to have a superb quantity of lively nodes. Furthermore, the entire nodes are inclined to have particular software program and {hardware} instruments for mining as a result of that’s the way you validate a transaction in PoW.
The rule of one of these community is full decentralization. So, customers wouldn’t be a part of a bunch and would observe all the foundations of the system. Moreover, to ensure the decentralized nature prevails, each node affords a computation energy however not sufficient to overpower anybody else.
Nonetheless, if a hacker can use a blockchain hack device to get extra computing energy, then he can launch an assault. However to try this, he wants to manage 51% of the general computational energy throughout the system. By doing so, they will increased hash charge in comparison with different nodes.
In the long term, they will manipulate the transaction course of, and that might result in double spend. Nonetheless, this may solely happen in power-hungry consensus algorithms that take care of computational powers.
Unsure the right way to construct your profession in enterprise blockchains? Enroll Now in Construct Your Profession in Enterprise Blockchains Course
Can Hackers Pull It Off?
In actuality, public blockchains akin to Ethereum comes with a excessive variety of nodes. The extra nodes the community provides up, the extra computational energy is required. Moreover, new nodes are including to the community each single day.
This excessive stage of computational energy ensures that hacking blockchain could be a slightly tough process. Primarily as a result of the blockchain hack device they’ll be utilizing isn’t able to providing this a lot computational energy to beat different nodes.
Additionally, any platform not utilizing PoW is on the secure aspect, and if it’s personal or federated, you then’re within the clear for certain.
Not so fashionable public blockchains may be the principle goal right here. In 2018, the hackers tried to drag a 51% hack blockchain assault on Monacoin, Verge, and so on.
Need to know the distinction between PoW Vs PoS? Learn right here PoW Vs. PoS: A Comparability Between Two Blockchain Consensus Algorithms
Does It Profit the Hackers in Any Means?
If a public blockchain isn’t that fashionable, then the worth of its cryptocurrency could be low. Via a 51% assault, they might undoubtedly get cash, however the revenue could be a lot decrease. Then again, the hacking blockchain of a preferred public platform would require a substantial variety of computational powers, and in the long term, it might value greater than the revenue.
-
Blockchain Protocol Code Bugs
One other instance on this hack blockchain information could be any flaws within the protocol supply codes. Properly, the blockchain is an advanced system, and that may have bugs within the protocol codes, as nicely. Let’s see an instance of this challenge to know it higher. This is likely one of the disadvantages of blockchain.
There was a blockchain hack situation in 2010, the place they misused a nasty code within the Bitcoin protocol. In actuality, the code that checked Bitcoin transactions had been defective. Apparently, the code doesn’t work if the result is just too massive, and it causes an overflow in summing up.
Consequently, a hacker used it to his/her benefit and generated 184.467 billion cash. Nonetheless, the utmost provide of Bitcoins is definitely 21 million! After discovering out, the creator Satoshi Nakamoto and one other developer Gavin Andersen shortly mounted the problems inside just some hours.
Moreover, they forked the unhealthy chain to create a superb chain and suggested different customers to keep away from the chain created by the hacker. All in all, it was a superb save.
However we’ve got to say, somebody doing an identical hack blockchain scheme utilizing the identical methodology is sort of unpredictable at current.
Anybody desirous to assault utilizing a bug like this has to have a complicated stage of expertise even to establish the problem, not to mention make modifications to it. As blockchain is a classy platform, it’s fairly unimaginable.
Additionally, now, blockchain builders totally verify their codes earlier than launching, and that forestalls this sort of a multitude successfully.
That is one other defective code scenario that may result in hack blockchain situations. It’s extra of a hacking a program within the community slightly than the entire platform itself. Nonetheless, this sort of blockchain hack can depart a severe affect.
Good contracts are awfully fashionable and run on numerous blockchain platforms. In the event you predefine the circumstances, it may switch belongings primarily based on these guidelines. Additionally, as they’re on the blockchain, then nobody can modify them as soon as the phrases are set.
Moreover, in any case, circumstances are met, it may execute routinely, and people additionally get a everlasting place within the ledger. So, nobody can really reverse the execution. Nonetheless, if someway, the sensible contract code is filled with bugs, then hackers might exploit that.
instance could be the assault on DAO. Throughout 2016, the Ethereum neighborhood created DAO to control funding funds and assist them higher handle proposals. Nonetheless, they had been utilizing sensible contracts to handle the DAO.
Though the Ethereum system protocol was working completely, the sensible contract program had a bug. In actuality, the bug allowed a consumer to request cash from the DAO account and never file it on the ledger. Such a DAO hack poses an amazing risk to blockchain safety.
Hacker bought maintain of it and took $60 million from the community. After this incident, Ethereum onerous forked to reset the system. So, the Ethereum you see now is definitely the results of that onerous fork. Nonetheless, some folks nonetheless use the previous chain, and that’s known as Ethereum Traditional.
By way of these, different questions akin to can blockchain wallets be hacked or different companies referring to blockchain be hacked rise. Now we have to say, it’s the identical for all the things else as nicely.
Excited to be taught concerning the vital vulnerabilities and safety dangers in sensible contract improvement, Enroll now within the Good Contracts Safety Course!
It’s one other form of assault the place an entity can have an enormous variety of nodes inside a single community. With the variety of nodes, the entity can try to flood the community with unhealthy transactions or invalid ones and disrupt the exercise.
Hackers can use the varied blockchain hack device for this one. Nonetheless, you must know this assault remains to be theoretical. Nonetheless, stopping it’s a lot less complicated. If the enterprise blockchain platforms could make proudly owning an enormous variety of nodes costly utilizing protocols and algorithms, then we are able to safely say the hackers can’t launch an assault.
It’s extra of an inner assault slightly than coming from the surface. A compromised Web Service Supplier is the basis explanation for one of these hack. Hackers can intercept the communication channels of blockchain by compromising or working with the ISP.
Though it’s attainable to run nodes from anyplace on this planet, nevertheless, within the present scenario, working nodes is very centralized. These ISPs have a tendency to hold out the load of the traffics, and these entry factors are susceptible.
Intercepting alerts on these channels would disrupt the communication and may then manipulate the transaction course of. Additionally, hackers can partition the community into separate items and spend cash on the great in a type of. Later, after they take away the partition, the smaller chain would get routinely canceled.
So far as it goes, there have been no experiences of such assaults thus far.
Right here, the hackers can flood a community with excessive volumes of site visitors and disrupt the respectable requests from getting any assets. We predict you see this sort of assault every day on centralized enterprises.
In actuality, the tactic is to maintain sending numerous requests to the corporate’s server, not giving it time to deal with the elevated site visitors surge. Consequently, the bandwidth runs out, and the server crashes.
Nonetheless, WE wish to level out, hackers can’t really steal something slightly than simply inflicting hurt to the community exercise. Extra so, many blockchain options can safeguard it from this sort of assault effectively.
Hacking the Blockchain or Crypto Exchanges?
As you already noticed that a lot of the examples of hacking the blockchain are primarily of a crypto trade or any platform that occurs to supply cryptocurrencies. Thus, a lot of the newcomers are inclined to confuse these crypto trade hacks and hack blockchain.
Nonetheless, you must know there’s a little bit of distinction between these two. Let’s see why they’re totally different –
In actuality, a lot of the public blockchains have very totally different know-how structure than one another. And so, they aren’t interoperable. Due to this fact, you may’t really transact on the bitcoin platform utilizing Ethereum.
Thus, that is the place the crypto exchanges come into play. In actuality, these give you a platform the place you should utilize nearly any form of cryptocurrency. You possibly can even convert a cryptocurrency into one other. Though they make it simpler, nevertheless, they’re third-party service suppliers.
Thus, buying and selling could be very simple; nevertheless, they don’t have the mandatory quantity of safety for his or her centralized servers. And this manner, hackers utilizing blockchain hack device can simply hack these tokens with none points. In actuality, you could find blockchain dangers when you begin to use it.
Nonetheless, after they do assault these crypto exchanges, it doesn’t imply that they’re hacking the blockchain. As a substitute, it’s simply an assault on the central server and isn’t thought of hacking the blockchain know-how.
Let’s transfer onto our subsequent section on this can blockchain be hacked information.
Customers Are Equally to Blame or Even Extra!
When somebody asks, “can blockchain be hacked,” the reply could be between a gray space. Nonetheless, in each case, you’ll see that usually, customers are accountable, and generally they’re the entire purpose why blockchain hack occurs within the first place.
In actuality, blockchain know-how does provide fairly a sturdy system, and there have been only some profitable circumstances of a hack blockchain scenario. Nonetheless, most occasions, customers lose an unlimited sum of money. However how?
Properly, the safety in blockchain know-how is sort of sturdy, to start with. Nonetheless, you’re forgetting about essentially the most susceptible entry level of the system – the customers.
You may be pondering, can blockchain pockets be hacked, and I’d must say – YES!
Numerous entry factors akin to exchanges, wallets, different third-party companies that the customers use are inclined to have a susceptible safety protocol. Additionally, many customers don’t even the distinction between a personal key and a public key. Due to this fact, they will reveal their personal keys to others and lose all of their belongings.
Curious concerning the variations between personal and public keys? Right here’s a information to personal key vs public key.
Thus, hackers can simply use a blockchain hack device to hack into the system and steal tens of millions of belongings.
Now we have to say that a lot of the situations that we included on this hack blockchain information are theoretical. Even in order that that blockchain platforms are defending these with none points in real-time. The excessive stage of crypto hacking primarily occurred as a result of, nicely, people aren’t’ so nice at being vigilant.
Many customers are inclined to reuse passwords, function the web carelessly, fall sufferer to phishing scams, neglect any uncommon behaviors, use their gadgets in susceptible locations, and so forth. All of those can result in hack blockchain schemes fairly simply.
Additionally Test: Understanding European Blockchain Companies Infrastructure (EBSI)
Can You Actually Defeat the Hackers?
There are numerous current startups and enterprises which might be addressing the problem of blockchain hacks. Furthermore, there are some definitive methods to enhance the general safety of the structure. Nonetheless, builders and customers each have an enormous play on this. Extra so, blockchain options undoubtedly can assist out in defeating the hacker if you happen to use it in the suitable means. Let’s see what these are –
- Auditing – Auditing processes that might verify blockchain protocol codes closely earlier than launching. Any form of false or unhealthy code could be detected fairly simply. Extra so, if you happen to can carry AI into the combo, it might be extremely correct.
- Check Exhaustively – Good contract codes needs to be examined exhaustingly to eliminate any loopholes. With out 1000’s of real-time exams, nobody can determine if it has any bugs or not.
- Privateness – Customers have to preserve their personal key personal and never share it with anybody else. There’s really no telling from the place your personal keys can leak. So, preserve it in a secure place away from everybody else.
- Vigilance – Customers shouldn’t use repetitive passwords or log in from a international system. It could give a hacker an opportunity to misuse your account.
- Monitoring Choices – Blockchain platforms ought to have monitoring choices to detect any irregular actions quick.
- Up-to-date – Blockchain Safety protocols needs to be up-to-date as quick as attainable. It can make sure that there could be no vulnerability from the software program perspective.
- Consensus Algorithms – Blockchain ought to use anti-hack consensus algorithms.
- Fixed Reviews – Customers on the community ought to report any bug on the system as quickly as they detect it. If the customers deal with the system as their very own, then it might keep secured for them as nicely.
Enroll Now: Licensed Enterprise Blockchain Architect (CEBA)
Ending Observe
Properly, can blockchain be hacked or not is a slightly sophisticated query, to start with? The know-how itself is way extra superior to any others on the market thus far. And as we all know, it’s nonetheless fairly new to the tech membership. Thus, it’ll undoubtedly have some flaws as nicely.
Nonetheless, most of its flaws may be overcome if blockchain corporations begin to take into account high quality over amount.
On that notice, many enterprise blockchains now provide the best stage of safety with out all the failings. They usually do appear fairly promising thus far. Hopefully, these platforms can fend of hack blockchain conditions with none points.
Now that you recognize concerning the dangers, what are your subsequent steps? Do you need to turn out to be a blockchain safety skilled in coping with all these points? Enroll in our Licensed Blockchain Safety Skilled (CBSE) course and learn to resolve all the safety points directly!
*Disclaimer: The article shouldn’t be taken as, and isn’t supposed to offer any funding recommendation. Claims made on this article don’t represent funding recommendation and shouldn’t be taken as such. 101 Blockchains shall not be chargeable for any loss sustained by any one who depends on this text. Do your personal analysis!