Decentralization, n. The safety assumption {that a} nineteen yr outdated in Hangzhou and somebody who’s possibly within the UK, and possibly not, haven’t but determined to collude with one another.
There was a considerable amount of ruckus prior to now week concerning the problem of mining centralization within the Bitcoin community. We noticed a single mining pool, GHash.io, amass over 45% hashpower for a lot of hours, and at one level even develop to turn into 51% of your complete community. The complete entrance web page of the Bitcoin reddit was ablaze in intense dialogue and a uncommon conflict of complacency and worry, miners shortly mobilized to take their hashpower off GHash, and surprisingly intelligent methods have been utilized in an try to deliver again the stability between the totally different swimming pools, as much as and together with one miner with “between 50 TH/s and a couple of PH/s” mining at GHash however refusing to ahead legitimate blocks, basically sabotaging all mines on the pool to the extent of as much as 4%. Now, the scenario has considerably subsided, with GHash all the way down to 35% community hashpower and the runner up, Discus Fish, as much as 16%, and it’s doubtless that the scenario will stay that approach for not less than a short time earlier than issues warmth up once more. Is the issue solved? In fact not. Can the issue be solved? That would be the main topic of this publish.
Bitcoin Mining
To begin with, allow us to perceive the issue. The aim of Bitcoin mining is to create a decentralized timestamping system, utilizing what is actually a majority vote mechanism to find out by which order sure transactions got here as a approach of fixing the double-spending drawback. The double-spending drawback is easy to elucidate: if I ship a transaction sending my 100 BTC to you, after which in the future later I ship a transaction sending the identical 100 BTC to myself, each of these transactions clearly can not concurrently course of. Therefore, one of many two has to “win”, and the intuitively right transaction that ought to get that honor is the one which got here first. Nevertheless, there is no such thing as a approach to have a look at a transaction and cryptographically decide when it was created. That is the place Bitcoin mining steps in.
Bitcoin mining works by having nodes referred to as “miners” combination current transactions and produce packages referred to as “blocks”. For a block to be legitimate, the entire transactions it comprises have to be legitimate, it should “level to” (ie. comprise the hash of) a earlier block that’s legitimate, and it should fulfill “the proof of labor situation” (specifically, SHA2562(block_header) <= 2190, ie. the double-hash of the block header should begin with numerous zeroes). As a result of SHA256 is a pseudorandom operate, the one technique to make such blocks is to repeatedly try to supply them till one occurs to fulfill the situation. The two190 “goal” is a versatile parameter; it auto-adjusts in order that on common your complete community must work for ten minutes earlier than one node will get fortunate and succeeds; as soon as that occurs, the newly produced block turns into the “newest” block, and everybody begins attempting to mine a block pointing to that block because the earlier block. This course of, repeating as soon as each ten minutes, constitutes the first operation of the Bitcoin community, creating an ever-lengthening chain of blocks (“blockchain”) containing, so as, the entire transactions which have ever taken place.
If a node sees two or extra competing chains, it deems the one that’s longest, ie. the one which has probably the most proof-of-work behind it, to be legitimate. Over time, if two or extra chains are concurrently at play, one can see how the chain with extra computational energy backing it’s finally assured to win; therefore, the system could be described as “one CPU cycle, one vote”. However there’s one vulnerability: if one social gathering, or one colluding group of events, has over 50% of all community energy, then that entity alone has majority management over the voting course of and might out-compute every other chain. This provides this entity some privileges:
- The entity can solely acknowledge blocks produced by itself as legitimate, stopping anybody else from mining as a result of its personal chain will at all times be the longest. Over time, this doubles the miner’s BTC-denominated income at everybody else’s expense. Word {that a} weak model of this assault, “selfish-mining“, begins to turn into efficient at round 25% community energy.
- The entity can refuse to incorporate sure transactions (ie. censorship)
- The entity can “return in time” and begin mining from N blocks in the past. When this fork inevitably overtakes the unique, this removes the impact of any transactions that occurred within the unique chain after the forking level. This can be utilized to earn a bootleg revenue by (1) sending BTC to an alternate, (2) ready 6 blocks for the deposit to be confirmed, (3) buying and withdrawing LTC, (4) reversing the deposit transaction and as a substitute sending these cash again to the attacker.
That is the dreaded “51% assault”. Notably, nevertheless, even 99% hashpower doesn’t give the attacker the privilege of assigning themselves an arbitrary variety of new cash or stealing anybody else’s cash (besides by reversing transactions). One other necessary level is that 51% of the community shouldn’t be wanted to launch such assaults; if all you need is to defraud a service provider who accepts transactions after ready N confirmations (normally,
N = 3or
N = 6), in case your mining pool has portion P of the community you’ll be able to succeed with likelihood
(P / (1-P))^N; at 35% hashpower and three confirmations, which means that GHash can presently steal altcoins from an altcoin alternate with 15.6% success likelihood – as soon as in each six tries.
Swimming pools
Right here is we get to swimming pools. Bitcoin mining is a rewarding however, unfortuantely, very high-variance exercise. If, within the present 100 PH/s community, you’re operating an ASIC with 1 TH/s, then each block you could have an opportunity of 1 in 100000 of receiving the block reward of 25 BTC, however the different 99999 instances out of 100000 you get precisely nothing. Provided that community hashpower is presently doubling each three months (for simplicity, say 12500 blocks), that offers you a likelihood of 15.9% that your ASIC will ever generate a reward, and a 84.1% likelihood that the ASIC’s complete lifetime earnings shall be precisely nothing.
A mining pool acts as a type of inverse insurance coverage agent: the mining pool asks you to mine into into its personal tackle as a substitute of yours, and for those who generate a block whose proof of labor is nearly ok however not fairly, referred to as a “share”, then the pool offers you a smaller fee. For instance, if the mining issue for the primary chain requires the hash to be lower than 2190, then the requirement for a share is perhaps 2190. Therefore, on this case, you’ll generate a share roughly each hundred blocks, receiving 0.024 BTC from the pool, and one time in a thousand out of these the mining pool will obtain a reward of 25 BTC. The distinction between the anticipated 0.00024 BTC and 0.00025 BTC per block is the mining pool’s revenue.
Nevertheless, mining swimming pools additionally serve one other goal. Proper now, most mining ASICs are highly effective at hashing, however surprisingly weak at every thing else; the one factor they usually have for basic computation is a small Raspberry Pi, far too weak to obtain and validate your complete blockchain. Miners might repair this, at the price of one thing like an additional 0 is lower than $100. As an alternative, they ask mining swimming pools to generate mining information for them. The “mining information” in query refers back to the block header, just a few hundred bytes of information containing the hash of the earlier block, the foundation of a Merkle tree containing transactions, the timestamp and another ancillary information. Miners take this information, and proceed incrementing a price referred to as a “nonce” till the block header satisfies the proof-of-work situation. Ordinarily, miners would take this information from the block that they independently decide to be the newest block; right here, nevertheless, the precise number of what the newest block is is being relegated to the swimming pools.
Thus, what do we now have? Properly, proper now, basically this:
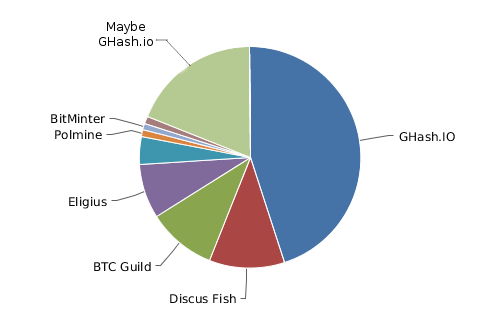
The mining ecosystem has solidified into a comparatively small variety of swimming pools, and each has a considerable portion of the community – and, after all, final week a kind of swimming pools, GHash, reached 51%. Given that each time any mining pool, whether or not Deepbit in 2011 or GHash in 2013, reached 51% there was a sudden large discount within the variety of customers, it’s solely doable that GHash truly received wherever as much as 60% community hashpower, and is solely hiding a few of it. There may be loads of proof in the true world of huge companies creating supposedly mutually competing manufacturers to offer the looks of selection and market dynamism, so such a speculation ought to by no means be discounted. Even assuming that GHash is in actual fact being trustworthy concerning the degree of hashpower that it has, what this chart actually says is that the one motive why there will not be 51% assaults taking place in opposition to Bitcoin proper now’s that Discus Fish, a mining pool run by a nineteen-year-old in Hangzhou, China, and GHash, a mining pool run supposedly within the UK however might be wherever, haven’t but determined to collude with one another and take over the blockchain. Alternatively, if one is inclined to belief this explicit nineteen-year-old in Hangzhou (in any case, he appeared fairly good once I met him), Eligius or BTCGuild can collude with GHash as a substitute.
So what if, for the sake of instance, GHash will get over 51% once more and begins launching 51% assaults (or, maybe, even begins launching assaults in opposition to altcoin exchanges at 40%)? What occurs then?
To begin with, allow us to get one unhealthy argument out of the best way. Some argue that it doesn’t matter if GHash will get over 51%, as a result of there is no such thing as a incentive for them to carry out assaults in opposition to the community since even one such assault would destroy the worth of their very own forex items and mining {hardware}. Sadly, this argument is solely absurd. To see why, take into account a hypothetical forex the place the mining algorithm is solely a signature verifier for my very own public key. Solely I can signal blocks, and I’ve each incentive to take care of belief within the system. Why would the Bitcoin group not undertake my clearly superior, non-electricity-wasteful, proof of labor? There are a lot of solutions: I is perhaps irrational, I’d get coerced by a authorities, I’d begin slowly inculcating a tradition the place transaction reversals for sure “good functions” (eg. blocking baby pornography funds) are acceptable after which slowly develop that to cowl all of my ethical prejudices, or I’d actually have a large brief in opposition to Bitcoin at 10x leverage. These center two arguments will not be loopy hypotheticals; they’re real-world documented actions of the implemenation of me-coin that already exists: PayPal. Because of this decentralization issues; we don’t burn tens of millions of {dollars} of electrical energy per yr simply to maneuver to a forex whose continued stability hinges on merely a barely totally different type of political recreation.
Moreover, you will need to notice that even GHash itself has a historical past of involvement in utilizing transaction reversal assaults in opposition to playing websites; particularly, one might recall the episode involving BetCoin Cube. In fact, GHash denies that it took any deliberate motion, and might be right; somewhat, the assaults appear to be the fault of a rogue worker. Nevertheless, this isn’t an argument in favor of GHash; a lot the alternative, it’s a piece of real-world empirical proof displaying a standard argument in favor of decentralization: energy corrupts, and equally importantly energy attracts those that are already corrupt. Theoretically, GHash has elevated safety since then; in follow, it doesn’t matter what they do that central level of vulnerability for the Bitcoin community nonetheless exists.
Nevertheless, there’s one other, higher, argument for why mining swimming pools will not be a problem: specifically, exactly the truth that they don’t seem to be particular person miners, however somewhat swimming pools from which miners can enter and depart at any time. Due to this, one can fairly say that Ars Technica’s declare that Bitcoin’s safety has been “shattered by an nameless miner with 51% community energy” is totally inaccurate; there is no such thing as a one miner that controls something near 51%. There may be certainly a single entity, referred to as CEX.io, that controls 25% of GHash, which is frightening in itself however however removed from the situation that the headline is insinuating is the case. If people miners don’t wish to take part in subverting the Bitcoin protocol and inevitably knocking the worth of their cash down by one thing like 70%, they will merely depart the pool, and such a factor has now occurred thrice in Bitcoin’s historical past. Nevertheless, the query is, because the Bitcoin financial system continues to professionalize, will this proceed to be the case? Or, given considerably extra “grasping” people, will the miners carry on mining on the solely pool that lets them proceed incomes income, individually saving their very own income at the price of taking your complete Bitcoin mining ecosystem collectively down a cliff?
Options
Even now, there’s truly one technique that miners can, and have, taken to subvert GHash.io: mining on the pool however intentionally withholding any blocks they discover which are truly legitimate. Such a method is undetectable, however with a 1 PH/s miner mining on this approach it basically reduces the income of all GHash miners by about 2.5%. This type of pool sabotage utterly negates the advantage of utilizing the zero-fee GHash over different swimming pools. This means to punish unhealthy actors is fascinating, although its implications are unclear; what if GHash begins hiring miners to do the identical in opposition to each different pool? Thus, somewhat than counting on vigilante sabotage ways with an unexamined financial endgame, we should always ideally attempt to search for different options.
To begin with, there’s the ever-present P2P mining pool, P2Pool. P2Pool has been round for years, and works by having its personal inside blockchain with a 10-second block time, permitting miners to submit shares as blocks within the chain and requiring miners to try to supply blocks sending to the entire previous few dozen share producers on the identical time. If P2Pool had 90% community hashpower, the end result wouldn’t be centralization and benevolent dictatorship; somewhat, the limiting case would merely be a duplicate of the plain outdated Bitcoin blockchain. Nevertheless, P2Pool has an issue: it requires miners to be absolutely validating nodes. As described above, given the opportunity of mining with out being a totally validating node that is unacceptable.
One answer to this drawback, and the answer that Ethereum is taking, is to have a mining algorithm that forces nodes to retailer your complete blockchain domestically. A easy algorithm for this in Bitcoin’s case is:
def mine(block_header, N, nonce): o = [] for i in vary(20): o.append(sha256(block_header + nonce + i)) n = [] for i in vary(20): B = (o[i] / 2**128) % N n.append(tx(B, o[i])) return sha256(block_header + str(n))
The place tx(B, ok) is a operate that returns the kth transaction in block B, wrapping round modulo the variety of transactions in that block if crucial, and N is the present block quantity. Word that it is a easy algorithm and is very suboptimal; some apparent optimizations embrace making it serial (ie. o[i+1] depends upon n[i]), constructing a Merkle tree out of the o[i] values to permit them to be individually verified, and, because the Ethereum protocol already does, sustaining a separate state tree and transaction record so the algorithm solely wants to question the present block. The one minor roadblock to profitable implementation in Ethereum is solely that the present trie implementation has no idea of the “kth node” of a tree; the closest analog would in all probability have to be “first node with a key lexicographically after ok, with wraparound”, one thing for which it’s doable to supply a compact Patricia tree proof.
This truly solves two issues on the identical time. First, it removes the inducement to make use of a centralized pool as a substitute of P2Pool. Second, there’s an ongoing disaster in Bitcoin about how there are too few full nodes; the rationale why that is the case is that sustaining a full node with its 20GB blockchain is dear, and nobody needs to do it. With this scheme, each single mining ASIC can be compelled to retailer your complete blockchain, a state from which performing the entire capabilities of a full node turns into trivial.
A second technique is one other cryptographic trick: make mining non-outsourceable. Specificically, the thought is to create a mining algorithm such that, when a miner creates a legitimate block, they at all times essentially have another approach of publishing the block that secures the mining reward for themselves. The technique is to make use of a cryptographic building referred to as a zero-knowledge proof, cryptographically proving that they created a legitimate block however preserving the block information secret, after which concurrently create a block with out proof of labor that sends the reward to the miner. This might make it trivial to defraud a mining pool, making mining swimming pools non-viable.
Such a setup would require a considerable change to Bitcoin’s mining algorithm, and makes use of cryptographic primitives way more superior than these in the remainder of Bitcoin; arguably, complexity is in itself a critical drawback, and one that’s maybe value it to resolve critical issues like scalability however to not implement a intelligent trick to discourage mining swimming pools. Moreover, making mining swimming pools unattainable will arguably make the issue worse, not higher. The explanation why mining swimming pools exist is to take care of the issue of variance; miners will not be keen to buy an funding which has solely a 15% likelihood of incomes any return. If the opportunity of pooling is unattainable, the mining financial system will merely centralize right into a smaller set of bigger gamers – a setup which, not like now, particular person individuals can not merely change away from. The earlier scheme, then again, nonetheless permits pooling so long as the native node has the complete blockchain, and thereby encourages a type of pooling (specifically, p2pool) that isn’t systemically dangerous.
One other strategy is much less radical: do not change the mining algorithm in any respect, however change the pooling algorithms. Proper now, most mining swimming pools use a payout scheme referred to as “pay-per-last-N-shares” (PPLNS) – pay miners per share an quantity primarily based on the income obtained from the previous few thousand shares. This algorithm basically splits the pool’s personal variance amongst its customers, leading to no threat for the pool and a small quantity of variance for the customers (eg. utilizing a pool with 1% hashpower, the anticipated commonplace deviation of month-to-month returns is ~15%, much better than the solo mining lottery however nonetheless non-negligible). Bigger swimming pools have much less variance, as a result of they mine extra blocks (by primary statistics, a pool with 4x extra mining energy has a 2x smaller commonplace deviation as a proportion). There may be one other scheme, referred to as PPS (pay-per-share), the place a mining pool merely pays a static quantity per share to miners; this scheme removes all variance from miners, however at the price of introducing threat to the pool; that’s the reason no mining pool does it.
Meni Rosenfeld’s Multi-PPS makes an attempt to offer an answer. As an alternative of mining into one pool, miners can try to supply blocks which pay to many swimming pools concurrently (eg. 5 BTC to 1 pool, 7 BTC to a different, 11.5 BTC to a 3rd and 1.5 BTC to a fourth), and the swimming pools pays the miner for shares proportionately (eg. as a substitute of 1 pool paying 0.024 BTC per share, the primary pool pays 0.0048, the second 0.00672, the third 0.01104 and the fourth 0.00144). This permits very small swimming pools to solely settle for miners giving them very small rewards, permitting them to tackle a degree of threat proportionate to their financial capabilities. For instance, if pool A is 10x greater than pool B, then pool A may settle for blocks with outputs to them as much as 10 BTC, and pool B may solely settle for 1 BTC. If one does the calculations, one can see that the anticipated return for pool B is strictly ten instances what pool A will get in each circumstance, so pool B has no particular superlinear benefit. In a single-PPS situation, then again, the smaller B would face 3.16x larger threat in comparison with its wealth.
The issue is, to what extent is the issue actually due to variance, and to what extent is it one thing else, like comfort? Positive, a 1% mining pool will see a 15% month-to-month commonplace deviation in its returns. Nevertheless, all mining swimming pools see one thing like a 40% month-to-month commonplace deviation of their returns merely due to the risky BTC worth. The distinction between 15% commonplace deviation and a couple of% commonplace deviation appears massive and a compelling motive to make use of the most important pool; the distinction between 42% and 55% not a lot. So what different elements may affect mining pool centralization? One other issue is the truth that swimming pools essentially “hear” about their very own blocks immediately and everybody else’s blocks after some community delay, so bigger swimming pools shall be mining on outdated blocks much less usually; this drawback is crucial for blockchains with a time of ten seconds, however in Bitcoin the impact is lower than 1% and thus insignificant. A 3rd issue is comfort; this will greatest be solved by funding an easy-to-use open-source make-your-own mining pool answer, in an analogous spirit to the software program utilized by many small VPS suppliers; if deemed necessary, we might find yourself partially funding a network-agnostic model of such an effort. The final issue that also stays, nevertheless, is that GHash has no price; somewhat, the pool sustains itself by means of its connection to the ASIC cloud-mining firm CEX.io, which controls 25% of its hashpower. Thus, if we wish to actually get all the way down to the underside of the centralization drawback, we may have to have a look at ASICs themselves.
ASICs
Initially, Bitcoin mining was supposed to be a really egalitarian pursuit. Tens of millions of customers all over the world would all mine Bitcoin on their desktops, and the end result can be concurrently a distribution mannequin that’s extremely egalitarian and broadly spreads out the preliminary BTC provide and a consensus mannequin that features hundreds of stakeholders, just about precluding any chance of collusion. Initially, the scheme labored, making certain that the primary few million bitcoins received broadly unfold amongst many hundreds of customers, together with even the usually cash-poor highschool college students. In 2010, nevertheless, got here the appearance of mining software program for the GPU (“graphics processing unit”), profiting from the GPU’s large parallelization to attain 10-100x speedups and rendering CPU mining utterly unprofitable inside months. In 2013, specialization took an extra flip with the appearance of ASICs. ASICs, or application-specific built-in circuits, are specialised mining chips produced with a single goal: to crank out as many SHA256 computations as doable as a way to mine Bitcoin blocks. Because of this specialization, ASICs get an extra 10-100x speedup over GPUs, rendering GPU mining unprofitable as nicely. Now, the one technique to mine is to both begin an ASIC firm or buy an ASIC from an current one.
The best way the ASIC firms work is easy. First, the corporate begins up, does some minimal quantity of setup work and figures out its plan, and begins taking preorders. These preorders are then used to fund the event of the ASIC, and as soon as the ASICs are prepared the units are shipped to customers, and the corporate begins manufacturing and promoting extra at an everyday tempo. ASIC manufacturing is completed in a pipeline; there’s one kind of manufacturing facility which produces the chips for ASICs, after which one other, much less refined, operation, the place the chips, along with commonplace elements like circuit boards and followers, are put collectively into full packing containers to be shipped to purchasers.
So the place does this depart us? It is apparent that ASIC manufacturing is pretty centralized; there are one thing like 10-30 firms manufacturing these units, and every of them have a big degree of hashpower. Nevertheless, I didn’t understand simply how centralized ASIC manufacturing is till I visited this unassuming little constructing in Shenzhen, China:

On the third ground of the manufacturing facility, we see:


What we now have within the first image are about 150 miners of 780 GH/s every, making up a complete 120 TH/s of miners – greater than 0.1% of complete community hashpower – multi functional place. The second image reveals packing containers containing one other 150 TH/s. Altogether, the manufacturing facility produces barely greater than the sum of those two quantities – about 300 TH/s – each single day. Now, have a look at this chart:
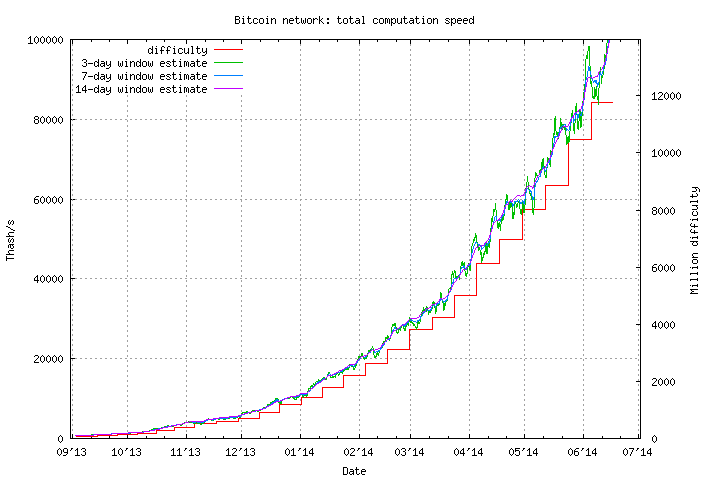
In complete, the Bitcoin community good points about 800 TH/s day by day. Thus, even including some security elements and assuming the manufacturing facility shuts down some days every week, what we now have is one single manufacturing facility producing over 1 / 4 of all new hashpower being added to the Bitcoin community. Now, the constructing is a bit massive, so guess what’s on the primary ground? That is proper, a fabrication facility producing Scrypt ASICs equal to 1 / 4 of all new hashpower added to the Litecoin community. This tasks a picture of a daunting endgame for Bitcoin: the Bitcoin community spending tens of millions of {dollars} of electrical energy yearly solely to exchange the US greenback’s mining algorithm of “8 white guys” with just a few dozen guys in Shenzhen.
Nevertheless, earlier than we get too alarmist about the way forward for mining, you will need to dig down and perceive (1) what’s fallacious with ASICs, (2) what’s okay with CPUs, and (3) what the way forward for ASIC mining goes to appear to be. The query is a extra advanced one than it appears. To begin with, one may ask, why is it unhealthy that ASICs are solely produced by just a few firms and 1 / 4 of them move by means of one manufacturing facility? CPUs are additionally extremely centralized; built-in circuits are being produced by solely a small variety of firms, and almost all computer systems that we use have not less than some elements from AMD or Intel. The reply is, though AMD and Intel produce the CPUs, they don’t management what’s run on them. They’re general-purpose units, and there’s no approach for the producers to translate their management over the manufacturing course of into any type of management over its use. DRM-laden “trusted computing modules” do exist, however it is vitally tough to think about such a factor getting used to power a pc to take part in a double-spend assault.
With ASIC miners, proper now issues are nonetheless not too unhealthy. Though ASICs are produced in solely a small variety of factories, they’re nonetheless managed by hundreds of individuals worldwide in disparate information facilities and houses, and particular person miners every normally with lower than just a few terahashes have the flexibility to direct their hashpower wherever they want. Quickly, nevertheless, which will change. In a month’s time, what if the producers understand that it doesn’t make financial sense for them to promote their ASICs once they can as a substitute merely maintain all of their units in a central warehouse and earn the complete income? Delivery prices would drop to near-zero, transport delays would go down (one week transport delay corresponds to ~5.6% income loss at present hashpower development charges) and there can be no want to supply secure or fairly casings. In that situation, it might not simply be 25% of all ASICs which are produced by one manufacturing facility in Shenzhen; it might be 25% of all hashpower run out of one manufacturing facility in Shenzhen.
When visiting the headquarters of an organization in Hangzhou that’s concerned, amongst different issues, in Litecoin mining, I requested the founders the identical query: why do not you simply maintain miners in-house? They offered three solutions. First, they care about decentralization. That is easy to know, and could be very lucky that so many miners really feel this fashion in the meanwhile, however finally mining shall be carried out by corporations that care a little bit extra about financial revenue and fewer about ideology. Second, they want pre-orders to fund the corporate. Affordable, however solvable by issuing “mining contracts” (basically, crypto-assets which pay out dividends equal to a selected variety of GH/s of mining energy). Third, there’s not sufficient electrical energy and house within the warehouses. The final argument, as specious because it appears, could be the just one to carry water in the long run; it’s also the acknowledged motive why ASICminer stopped mining purely in-house and began promoting USB miners to shoppers, suggesting that maybe there’s a robust and common rationale behind such a call.
Assuming that the funding methods of promoting pre-orders and promoting mining contracts are economically equal (which they’re), the equation for figuring out whether or not in-house mining or promoting makes extra sense is as follows:
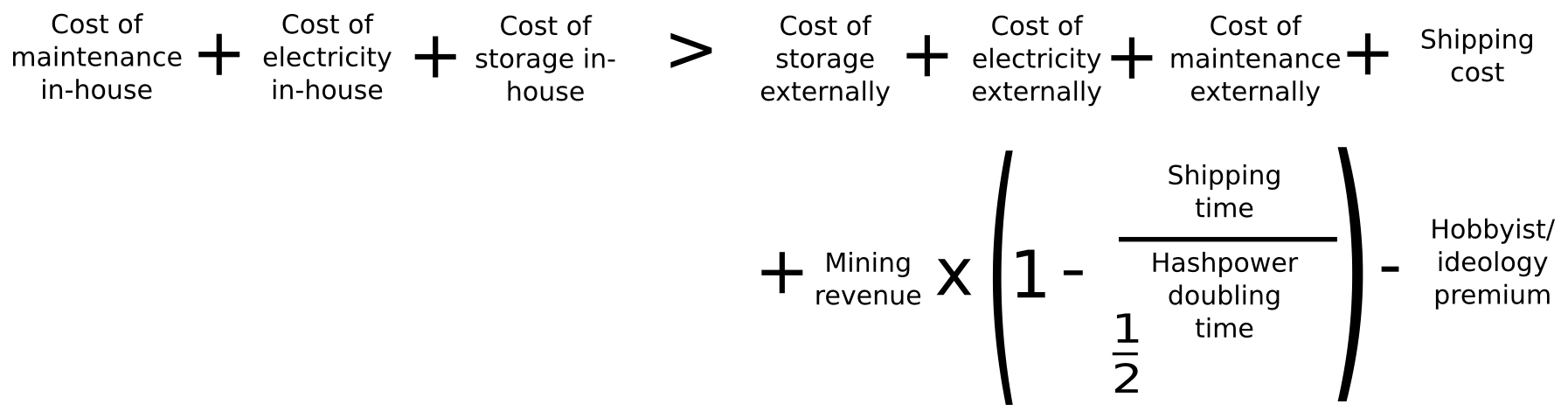
On the left aspect, we now have the prices of in-house mining: electrical energy, storage and upkeep. On the appropriate aspect, we now have the price of electrical energy, storage and upkeep externally (ie. in patrons’ palms), transport and the penalty from having to begin operating the ASIC later, in addition to a unfavourable issue to account for the truth that some folks mine not less than partially for enjoyable and out of an ideological want to assist the community. Let’s analyze these figures proper now. We’ll use the Butterfly Labs Monarch as our instance, and maintain every ASIC operating for one yr for simplicity.
- Inside electrical energy, storage, upkeep – in keeping with BFL’s checkout web page, inside electrical energy, storage and maintennance value $1512 per yr, which we’ll mark all the way down to $1000 assuming BFL takes some revenue
- Exterior electrical energy – in Ontario, costs are about $0.1 per KwH. A Butterfly Labs Monarch will run 600 GH/s at 350 W; normalizing this to per-TH, this implies an electrical energy value of $1.40 per day or $511 for your complete yr
- Exterior storage – at dwelling, one can take into account storage free, or one can add a comfort price of $1 per day; therefore, we’ll say someplace from $0 to $365
- Exterior upkeep – exhausting to quantify this worth; for technically expert invididuals who benefit from the problem it is zero, and for others it is perhaps exhausting; therefore, we are able to say $0 to $730
- Delivery value – in keeping with BFL, $38.
- Income – presently, 1 TH/s offers you 0.036 BTC or $21.6 per day. Since in our evaluation hashpower doubles each 90 days, so the effectiveness of the ASIC halves each 90 days, we get 122 days of life or $2562 income
- Delivery time – in keeping with my Chinese language sources, one week
- Hashpower doubling time – three months. Therefore, your complete expression for the transport delay penalty is 2562 * (1 – 0.5 ^ 0.0769) = 133.02
- Hobbyist/ideology premium – presently, a big portion of Bitcoin miners are doing it out of ideological concerns, so we are able to say wherever from $0 to $1000
Thus, including all of it up, on the left we now have $1000, and on the appropriate we now have $511 + $38 + $133 = $682, as much as plus $1095 and minus as much as $1000. Thus, it is solely ambiguous which one is best; errors in my evaluation and the nebulous variables of how a lot folks worth their time and aesthetics appear to far outweigh any particular conclusions. However what’s going to occur sooner or later? Essentially, one can count on that electrical energy, storage and upkeep can be less expensive centrally than with every client merely because of economies of scale and good points from specialization; moreover most individuals within the “actual world” will not be altruists, hobbyists or admirers of lovely ASIC coverings. Delivery value are above zero, and the transport delay penalty is above zero. So thus plainly the economics roundly favor centralized mining…
… aside from one potential issue: warmth. Proper now, ASICs are nonetheless in a speedy improvement part, so the overwhelming majority of the fee is {hardware}; the BFL miner used within the above instance prices 511. Sooner or later, nevertheless, improvement shall be a lot slower; finally we are able to count on a convergence to Moore’s regulation, with hashpower doubling each two years, and even Moore’s regulation itself appears to be slowing. In such a world, electrical energy prices might come again as the first choke level. However how a lot does electrical energy value? In a centralized warehouse, quite a bit, and the square-cube regulation ensures that in a centralized setting much more power than at dwelling would have to be spent on cooling as a result of the entire miners are in a single place and most of them are too deep contained in the manufacturing facility to have publicity to chill recent air. In a house, nevertheless, if the surface temperature is lower than about 20’C, the price of electrical energy is zero; all electrical energy spent by the miner essentially finally turns into “waste” warmth, which then heats the house and substitutes for electrical energy that will be spent by a central heater. That is the one argument for why ASIC decentralization may fit: somewhat than decentralization taking place as a result of everybody has a sure amount of unused, and thereby free, items of computational time on their laptop computer, decentralization occurs as a result of many individuals have a sure amount of demand for heating of their properties.
Will this occur? Many Bitcoin proponents appear satisfied that the reply is sure. Nevertheless, I’m not positive; it’s a wholly empirical query whether or not or not electrical energy value is lower than upkeep plus storage plus transport plus transport delay penalty, and in ten years’ time the equation might nicely fall on one aspect or the opposite. I personally am not keen to easily sit again and hope for the most effective. Because of this I personally discover it disappointing that so lots of the core Bitcoin builders (although happily not almost all) are content material to contemplate the proof of labor drawback “solved” or argue that making an attempt to resolve mining specialization is an act of “useless re-engineering”. It could show to be, or it might not, however the truth that we’re having this dialogue within the first place strongly means that Bitcoin’s present strategy could be very removed from excellent.
ASIC Resistance
The answer to the ASIC drawback that’s most frequently touted is the event of ASIC-resistant mining algorithms. To date, there have been two strains of thought in creating such algorithms. The primary is memory-hardness – lowering the ability of ASICs to attain large good points by means of parallelization through the use of a operate which takes a really great amount of reminiscence. The group’s first try was Scrypt, which proved to be not resistant sufficient; in January, I tried to enhance Scrypt’s memory-hardness with Dagger, an algorithm which is memory-hard to compute (to the extent of 128 MB) however simple to confirm; nevertheless, this algorithm is susceptible to shared-memory assaults the place quite a lot of parallel processes can entry the identical 128 MB of reminiscence. The present state-of-the-art in memory-hard PoW is Cuckoo, an algorithm which seems for length-42 cycles in graphs. It takes a considerable amount of reminiscence to effectively discover such cycles, however a cycle could be very fast to confirm, requiring 42 hashes and fewer than 70 bytes of reminiscence.
The second strategy is considerably totally different: create a mechanism for producing new hash capabilities, and make the house of capabilities that it generates so massive that the type of laptop greatest suited to processing them is by definition utterly generalized, ie. a CPU. This strategy will get near being “provably ASIC resistant” and thus extra future-proof, somewhat than specializing in particular points like reminiscence, nevertheless it too is imperfect; there’ll at all times be not less than some elements of a CPU that may show to be extraneous in such an algorithm and could be eliminated for effectivity. Nevertheless, the hunt shouldn’t be for excellent ASIC resistance; somewhat, the problem is to attain what we are able to name “financial ASIC resistance” – constructing an ASIC shouldn’t be value it.
That is truly surprisingly prone to be achievable. To see why, notice that mining output per greenback spent is, for most individuals, sublinear. The primary N items of mining energy are very low-cost to supply, since customers can merely use the prevailing unused computational time on their desktops and solely pay for electrical energy (E). Going past N items, nevertheless, one must pay for each {hardware} and electrical energy (H + E). If ASICs are possible, so long as their speedup over commodity {hardware} is lower than (H + E) / E, then even in an ASIC-containing ecosystem it will likely be worthwhile for folks to spend their electrical energy mining on their desktops. That is the aim that we want to try for; whether or not we are able to attain it or not is solely unknown, however since cryptocurrency as an entire is an enormous experiment in any case it doesn’t harm to strive.

